How the IP Tables Works in Linux
INTRODUCTIONS :
Firewall is an important step to take in securing any OS. All Linux distributions Included with a few firewall tools that we can use to configure our firewalls. In this guide, we’ll be covering the iptables firewall. It is a command line utility that uses policy chains to allow or block traffic.
Iptables is a standard firewall included in most Linux distributions by default. It is used to manage packet filtering and NAT rules. Understanding how to setup and configure iptables will help you manage your Linux firewall effectively.
In this tutorial we are going to discuss about how the IPTABLES works.
IPTABLES.SERVICE
The iptables service supports a local network firewall. It assumes total control of the iptables configuration. When it starts, it flushes and restores the complete iptables configuration. The restored rules are from its configuration file, /etc/sysconfig/iptables. The configuration file is not kept up to date during operation, so the dynamically added rules are lost during every restart.
# systemctl disable iptables.service # systemctl mask iptables.service
How Iptables Work :
Iptables is a command-line firewall utility that uses policy chains to allow or block traffic.
Types of Iptables and Chains
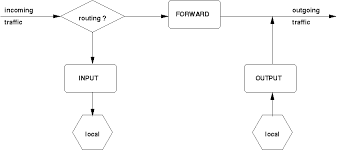
Iptables uses three different chains: input, forward, and output.
Input – This chain is used to control the behavior for incoming connections. Ex : if a user attempts to SSH into your PC/server, iptables will attempt to match the IP address and port to a rule in the input chain.
Forward – Packet for another NIC on the local server. For packets routed through the local server. Ex: Think of a router – data is always being sent to it but rarely actually destined for the router itself; the data is just forwarded to its target. Unless you’re doing some kind of routing, NATing, or something else on your system that requires forwarding, you won’t even use this chain.
Outpu – This chain is used for outgoing connections. Ex :if you try to ping howtogeek.com, iptables will check its output chain to see what the rules are regarding ping and howtogeek.com before making a decision to allow or deny the connection attempt.
Rules for IP Tables :
Rules contain a principle and a target.
If the principle is matched, it goes to the rules specified in the target (or) executes the special values mentioned in the target.
If the criteria is not matached, it moves on to the next rule.
Target Values :
Following are the possible special values that you can specify in the target.
ACCEPT – Firewall will accept the packet.
DROP – Firewall will drop the packet.
QUEUE – Firewall will pass the packet to the userspace.
RETURN – Firewall will stop executing the next set of rules in the current chain for this packet. The control will be returned to the calling chain.
At this point, the quickest way to learn about how iptables works is to use it to implement your own firewall 🙂
T H A N K I N G Y O U !!
