IP Tunneling
IP tunneling is a protocol used to communicate between two networks. It uses a different network protocol by encapsulating IP packets to transmit data. It is often used to connect two overlapping IP networks that don’t have a direct route to each other by using a basic routing protocol over an intermediate transport link.
IP tunnels are frequently used to connect two disjoint IP networks that don’t have a native routing path to each other using an underlying routable protocol over an intermediate transport network. In conjunction with the IPsec protocol, they can be used to create a virtual private network between two or more private networks across a public network such as the Internet. Another prominent use is to connect islands of IPv6 installations across the IPv4 Internet.
In IP tunneling, each IP packet, including the addressing information of its source and destination IP networks, is encapsulated in a different packet format native to the transit network.
Gateways are used at the borders between the source network and the transit network, and between the transit network and the destination network, to establish the endpoints of the IP tunnel across the transit network. This turns the IP tunnel endpoints into native IP routers that establish a standard IP route between the source and destination networks. Packets traversing these endpoints from the transit network are stripped of their transit frame format headers and trailers used in the tunneling protocol, converted to native IP format, and injected into the IP stack of the tunnel endpoints. In addition, any other protocol encapsulations used during transit, such as IPsec or Transport Layer Security, are removed.
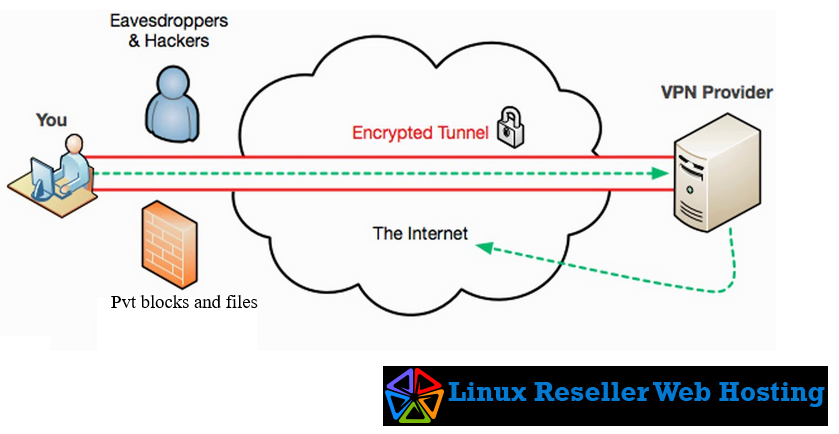
How IP Tunneling Works
- Encapsulation:
- The original data packet (e.g., an IPv4 packet) is wrapped inside another packet with a new header, creating an “encapsulated” packet.
- The outer header allows the encapsulated packet to traverse an intermediate network.
- Transmission:
- The encapsulated packet travels through the network using the protocol specified in the outer header.
- Decapsulation:
- At the tunnel endpoint, the outer header is removed, revealing the original packet for delivery to its destination.
Why Use IP Tunneling?
- Protocol Compatibility:
- Enables older or unsupported protocols to be used over modern or incompatible networks.
- Example: IPv6 packets encapsulated in IPv4 for networks that don’t support IPv6 natively.
- Secure Communication:
- Provides a way to create secure links (e.g., Virtual Private Networks, VPNs) by encrypting the inner packets.
- Network Interconnectivity:
- Allows private or isolated networks to connect over public networks like the Internet.
- Bypassing Restrictions:
- Facilitates communication through restricted or firewalled networks.
Types of IP Tunneling
- GRE (Generic Routing Encapsulation):
- A basic tunneling protocol for encapsulating a wide variety of network layer protocols.
- IPsec Tunnel Mode:
- Provides secure tunneling by encrypting the encapsulated packet for confidentiality and integrity.
- 6to4 Tunneling:
- Used to transport IPv6 packets over an IPv4 network.
- L2TP (Layer 2 Tunneling Protocol):
- Often combined with IPsec to provide secure VPN tunneling.
- MPLS (Multiprotocol Label Switching) Tunneling:
- Uses labels to direct packets through a predefined path, often for improving performance.
Example Use Cases
- Virtual Private Networks (VPNs):
- Securely connect remote devices or networks over the Internet using tunneling protocols like IPsec or L2TP.
- IPv6 over IPv4 Networks:
- Encapsulating IPv6 packets within IPv4 headers to enable IPv6 communication on older networks.
- Remote Access:
- Providing secure access to internal network resources for employees working from home.
- Bypassing Network Restrictions:
- Tunnels can bypass geo-blocking or network filtering by encapsulating traffic in another protocol.
Advantages of IP Tunneling
- Interoperability: Bridges different network types or protocols.
- Security: Can provide encryption for secure data transfer.
- Flexibility: Allows legacy systems to operate over modern networks.
Disadvantages of IP Tunneling
- Increased Overhead: Encapsulation adds extra headers, which can increase bandwidth usage.
- Complexity: Requires proper configuration and management.
- Performance Impact: Encryption and encapsulation can add latency.
To know about how to Troubleshooting Network Related Issues using NETSTAT Command click here.
