How to Secure Your Apache Web Servers
Hi All,
Today we are going to see how to secure your Apache web servers from the attackers. Apache is free and open source software. In the world 80% of websites running on Apache web server with cPanel background.
Normally Apache comes default settings which many not tweaking it and using it as it is. Now we are going to how secure it in many ways
- Assign unprivileged user for Apache
Most of the Linux distribution has got a default user named nobody. The idea behind running the apache with an unprivileged user is that, even if somebody compromises your web server, he should only be able to do whatever that user is permitted to do.

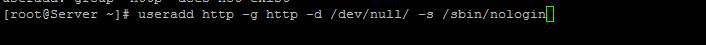
I have attached screen shots above to create unprivileged user and group for apache process
2. Use Minimalist HTTP configuration File
Apache configuration file very long, due to lot of comment sections on it. So there may be chance to miss out what option is enabled / disabled. So security experts suggestion is that keep your config file as possible as small, because you can easily identify which options are enabled or disabled.
3. Only Allow DocRoot To be Served
If Apache has read permission for a file, hackers can easily access the file by url encoding the request with characters like ..%2f & %2e%2e%5c to traverse directories and directly access the intended file
So only allow DocRoot to be served to all and keep others deny. Example code sniped shown on below

4. Do not Reveal Apache server information
Collecting information about a web server is the first thing that an intruder does. Apache by default will show its own version and system details, when it encounters a 404 or other such errors. The below configuration will not show those version information to others.

5. Allow only required HTTP methods
There are different types of HTTP methods, that a user agent sents to a server for different purposes. Some example’s of HTTP methods are mentioned below.
- GET
- POST
- PUT
- DELETE
- HEAD
- TRACE
You can only allow the require methods through limitexcept,the below code show how to do it.

Unfortunatly you cannot disable Trace through above method. To disable Trace please use the below method

6. Disable Directory listing in apache
If you do not have an index file inside your docroot, the default behavior of apache is to list the contents of that directory. Which means it will show all files inside that directory inside the browser itself. Like click and open/download them.
The below options directive can be used to disable directory listing in Apache.

7. Protection Against DOS Attacks in Apache.
As a server administrator, you have tune your Apache server to protect at-least minimal amount of DOS attack
The default timeout value is 300 seconds. That’s too long a time to wait for each connection made to the server. So let’s reduce it to something like 10 seconds.

Although its recommended to turn keepalive setting on, for performance reasons, the time in seconds for which the server will wait should be less, because an attacker can otherwise make a lot of connections and unnecessarily keep on resetting the timer, by sending junk requests. Hence lower the keepalive, higher the RAM on the server for new connections.

Hope this tutorial was helpful in achieving a basic security on your apache web server 🙂